FileSeal - offline file encryption
A lightweight, browser-based file encryption tool designed for local-only usage and zero server trust.
Project created on: 6 Dec. 2025 | Last updated: 29 Dec. 2025
FileSeal is a small, focused security project built to explore practical client-side encryption without relying on servers, accounts, or third-party services. All encryption and decryption happens entirely inside the browser, ensuring files never leave the user’s device.
The tool converts files into self-contained .fs containers using password-derived keys and modern
authenticated encryption. Each encrypted file includes the metadata required for safe restoration, without
exposing the original content.
FileSeal is intentionally minimal: no telemetry, no uploads, no backend, and no persistent state. The goal was clarity, correctness, and local control — not feature sprawl.
Overview
Problem
Many file encryption tools rely on native software installs, cloud storage, or opaque binaries. I wanted a transparent, browser-native solution that works offline and keeps files fully local.
Solution
A single-page, browser-based encryptor that derives keys from a user password and outputs a portable, self-describing encrypted container.
Core stack
Web Crypto API · AES-GCM · PBKDF2 · Vanilla JavaScript · HTML/CSS · Zero dependencies
Architecture
FileSeal follows a simple, linear flow: file ingestion, metadata preparation, encryption, and container assembly. The reverse path performs validation, decryption, and restoration.
- File input: Reads file bytes and captures basic metadata (name and MIME type).
- Key derivation: Derives a strong encryption key from the user password using PBKDF2 and a random salt.
- Encryption: Encrypts metadata and file bytes together using authenticated encryption.
- Container format: Prepends a small plaintext header containing magic bytes, version, salt, and IV.
- Restoration: Validates the container, decrypts payload, and restores the original file.
Key Features
Offline by design
Works entirely without network access. Files never leave the browser.
Authenticated encryption
Detects tampering and incorrect passwords during decryption.
Self-contained containers
Each encrypted file includes everything needed for safe restoration.
No dependencies
Uses native browser APIs only — no libraries, frameworks, or builds.
Minimal attack surface
No backend, no storage, no cookies, no persistent state.
Screenshots
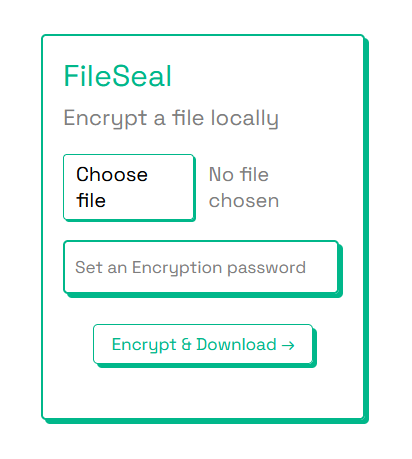
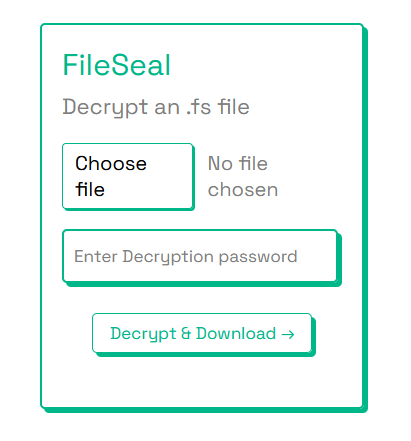
Sample code snippet
This snippet shows how a random IV and salt are generated before encryption:
// Generate randomness for each encryption const salt = crypto.getRandomValues(new Uint8Array(16)); const iv = crypto.getRandomValues(new Uint8Array(12)); // Derive key from password const key = await deriveKey(password, salt);
Possible future improvements
- Password strength estimation
- Streaming encryption for large files
- Multiple file support
- Container version upgrades
- Optional metadata minimization
Links
GitHub: https://github.com/grayguava/fileseal
Live Demo: https://fileseal.pages.dev/